Summary
- NetBeacon Measurement and Analytics Platform (MAP) observed two data records in March 2025: the highest number of unique domain names associated with phishing (47,613) and the largest month-on-month increase in unique domain names associated with phishing (63%).
- Most (87%) of this phishing was classified as ‘maliciously registered.’ The bulk of this malicious phishing was concentrated among a few registrars credentials.
- One registrar, Dominet HK Limited (IANA 3775), registered 55% of the identified unique domains (20,133) while managing less than 1% of all DUM. The second highest concentration was Gname.com Pte. Ltd. (IANA 1923) which held 9% (3,087 unique domains) while managing only 2% of total domains.
- We believe this concentration is linked to bulk malicious phishing campaigns which may be impacted by new policy approaches; see our White Paper for more details.
Record Highs in NetBeacon MAP Data
In March 2025 we observed two record highs in NetBeacon Measurement and Analytics Platform (MAP) data: the highest number of unique domain names associated with phishing (47,613), and the largest month-on-month increase in unique domain names associated with phishing (63%). See Figure 1: Aggregate Trends — Phishing. Most (87%) of this phishing was classified as ‘maliciously registered’ by our methodology. See Figure 2: Compromised vs Malicious — Phishing.
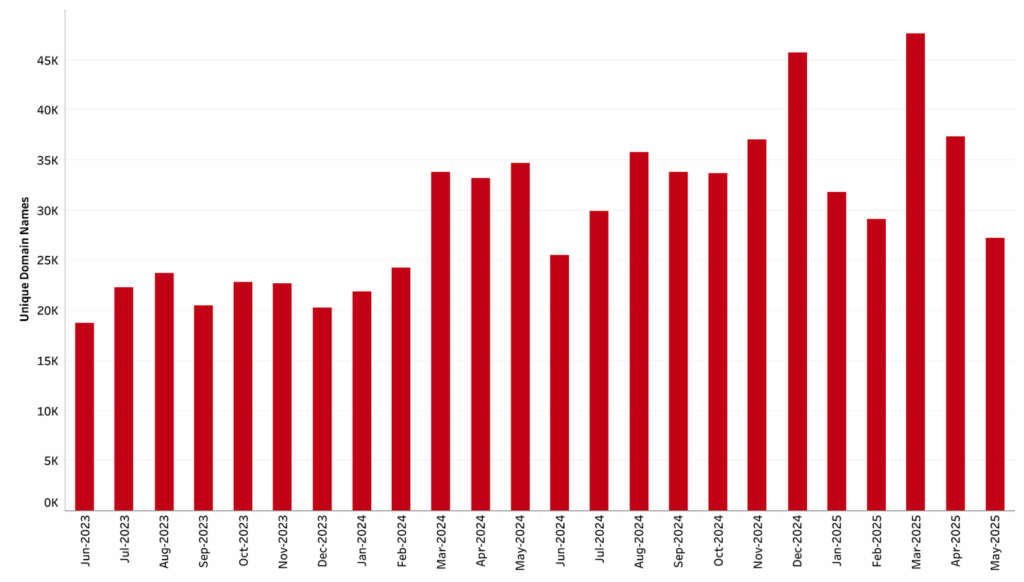
Figure 1: Aggregate Trends — Phishing
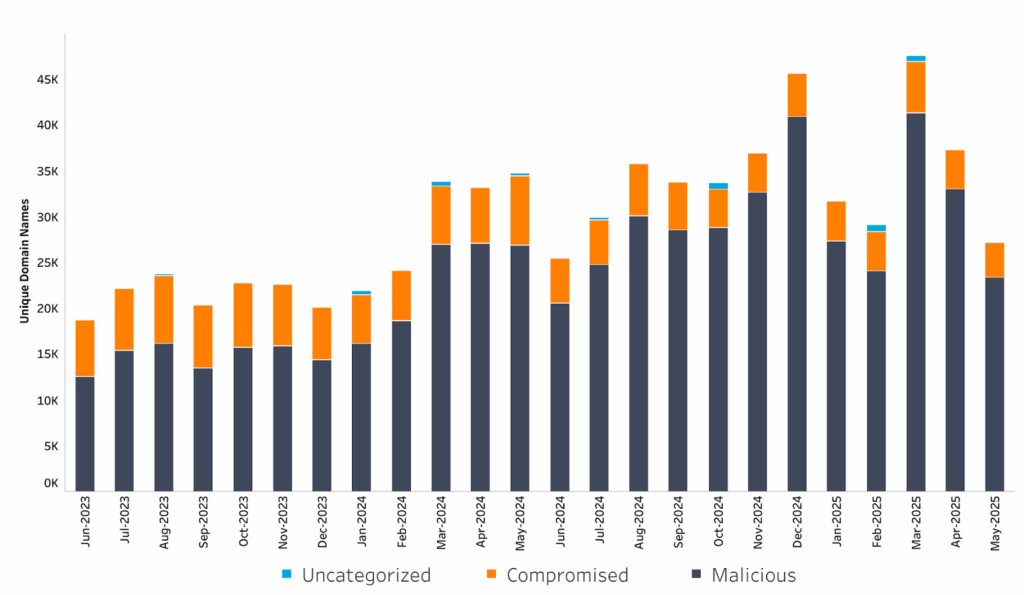
Figure 2: Compromised vs Malicious — Phishing
We found that the spike in malicious phishing was largely concentrated in two registrar credentials. For this portion of the analysis, we focused only on gTLD domain names, as they’re more reliably identified as registered with a particular registrar credential.
In March 2025, a single registrar (Dominet HK Limited, IANA 3775) registered 55% of the unique domains associated with phishing (20,133), while managing just 0.3% (640,480) of all gTLD DUM. The second-highest concentration was Gname.com Pte. Ltd. (IANA 1923) which registered 9% of unique phishing domains (3,087) while managing only 2% (4,672,094) of total gTLD domains. We refer to this imbalance as ‘over-indexing’: when a registrar credential accounts for a higher market share of malicious phishing than what they hold as a market share of domains. Most registrar credentials do not over-index on malicious phishing compared to their market share of domains, and of the ones that do, only around dozen per month over-index by more than 1%.
Both of these credentials are identified in our May 2025 Monthly Analysis report (which published March 2025 data), in ‘Table 3 Highest Observed Rates of Abuse (DUM)’. Gname.com Pte. Ltd is also featured in ‘Table 6 Highest Observed Rates of Abuse (New Registrations)’.
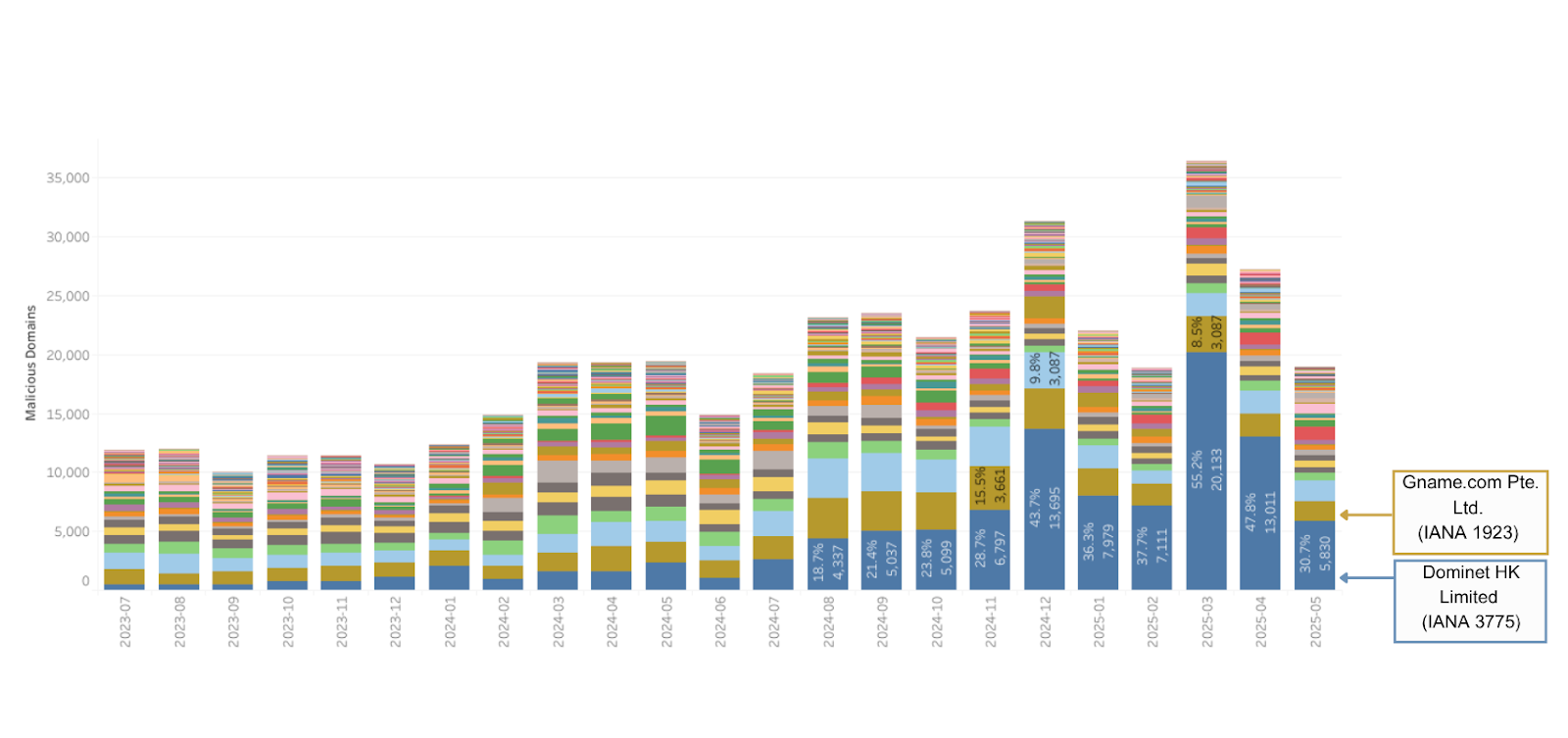
Figure 3: Malicious Phishing (Unique Domains) by Registrar: July 2023 – May 2025
This data indicates significant variations in the volume of malicious phishing attacks registrars are encountering. Reviewing the underlying domains, there are noticeable patterns in the alphanumeric domain string and registration date and time that indicate this concentration of activity is linked to large-scale malicious phishing campaigns, generally related to toll road scams.
Changing concentrations over time
These campaigns appear to have passed their peak, so we may begin to see new concentrations emerge. The next largest volume for malicious phishing in March 2025 was NameSilo, IANA 1479 (Figure 4). NameSilo hasn’t been named in our reports since February 2025 (which published December 2024 data) when they were featured in ‘Table 3: Highest observed rates of abuse’ for malicious phishing and malware. However, as the relative concentration of malicious phishing in Dominet and Gname subsided in May, NameSilo accounted for a larger proportion of the overall malicious phishing during the month (9%) which is an over-index relative to its domain market share (2%).
Recently, Web Commerce Communications Limited dba WebNic.cc (IANA 460) has featured regularly in ‘Table 3: Highest observed rates of abuse’ for malicious phishing and malware, and entered Table 6 in our July Report (May Data), which identifies registrar credentials with the highest observed rates of malicious phishing and malware as a percentage of new registrations. After NameSilo, WebNic.cc held the next largest percentage of malicious phishing May 2025 (6%), while managing less than 1% of the gTLD domain market.
Figure 4 shows a stacked bar chart of the percentage of unique domains identified as malicious phishing associated with each registrar credential over time. Note that the volume of unique domains varies month-to-month which has an impact on the percentage share (See Figure 3).
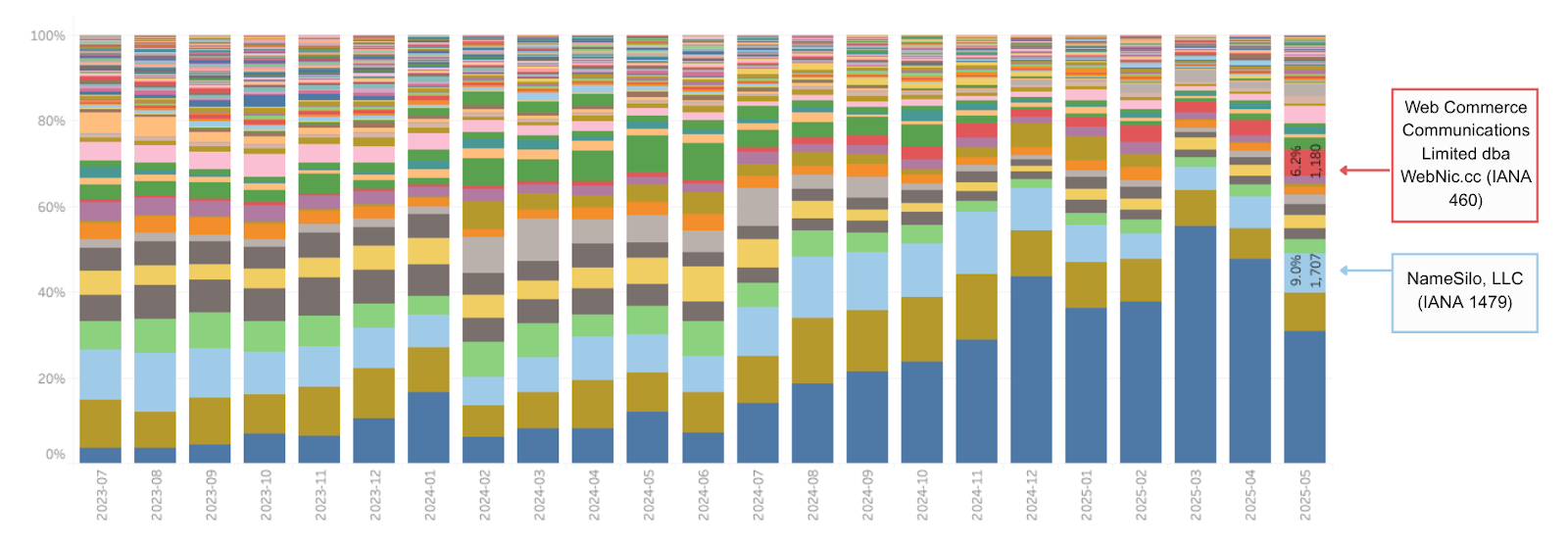
Figure 4: Malicious Phishing (% of Unique Domains) by Registrar Credential: July 2023 – May 2025
Typically, domain names registered with Dominet, Gname, Name Silo, and Webnic.cc record high rates of mitigation in our data, and relatively quick mitigation speeds. We measure mitigation activity up to 30 days at regular intervals, starting with minutes and extending into every 12 hours.
However, our measurement of mitigation is agnostic to attribution—that is, we don’t distinguish if it’s the registrar, the registry, the host, or any other actor who disrupts the use of the domain name from being used for harm. In addition, these types of malicious campaigns also move quickly, and typically anticipate disruption, which is why perpetrators register large batches as insulation against mitigation action. It is possible that even high rates of mitigation may leave a substantial window in which a malicious actor can cause significant harm. Measuring mitigation across the ecosystem is complex, there are various challenges involved, including evasion techniques to prevent detection via automated crawling. We continue to examine this data and will share more details on this as soon as possible.
Named registrars were notified prior to publication, responses are included in Note [2].
Addressing bulk malicious phishing campaigns
The fact that individual registrar credentials can be targeted with large volume campaigns is an indication to us at the Institute that the wider community should consider whether additional policy work is needed. While this particular malicious toll road campaign seems to be subsiding, there will surely be others that take their place.
Last year, gTLD registries and registrars formally voted in favour of changing their contracts with ICANN. This introduced new requirements on DNS Abuse that apply globally. These contracts are enforced by ICANN through ongoing compliance activity. We understand this occurs informally and formally, with many issues being resolved through engagement. When ICANN compliance deems it is necessary, a breach notice is issued. We note that one of the named registrars in this blog, Webnic.cc, was issued a formal notice of breach on 25 July 2025 for alleged “failure to comply with Section 3.18.2 of its RAA concerning Domain Name System (“DNS”) Abuse mitigation.
The 2024 gTLD amendments created an obligation for gTLD registrars and registries to act on individual well-evidenced reports of DNS Abuse, but we may need to go further to address high-volume mass malicious campaign registrations. One of the contributing factors to the 2024 amendments was the work of the gNSO Small Team who published recommendations in October 2022. The Small Team is once again reviewing this topic and we look forward to their recommendations.
As with all policy discussions, this deserves careful consideration and attention should be paid to unintended consequences. We have set out a number of ideas designed to tackle this policy challenge. In particular we focus on encouraging registrars to unearth coordinated malicious campaigns once they have one well-evidenced report, and discouraging ungated access to APIs for bulk registration of domains and/or account creation. Read our recent White Paper for more information on ideas for policy development to make the Internet a safer place.
Notes
[1] About NetBeacon MAP
Our analysis focuses on the ICANN registrar credential ecosystem, including only generic Top Level Domains (gTLDs). Data is sourced from NetBeacon MAP. Registrars and TLDs can also access free Individualized Dashboards for additional information on their own zones. NetBeacon MAP is delivered through a collaboration with KOR Labs, based out of Grenoble Alpes University in France. Data is collected in line with our methodology which sets out the various limitations of measurement. This methodology optimizes for accuracy over completeness, tracking phishing consistently across registrars and Top Level Domains (TLDs) over time, rather than attempting to capture all harm on the Internet.
One of our principles for NetBeacon MAP is transparency. In addition to publishing a methodology, we send notifications to all registrars and TLDs who are listed in our Monthly Analysis tables, even if they are redacted due to only appearing in the tables for a small number of months (our consistency principle). We also provided a copy of this blog to each named registrar in anticipation of publication for their information.
[2] Registrar Response
Prior to the publication of this blog Dominet (IANA 3775) indicated that they have recently implemented several solutions to mitigate abuse activity. We hope to see the impacts of these changes in future NetBeacon MAP data.